$11B Ethereum DAO hacker has been identified
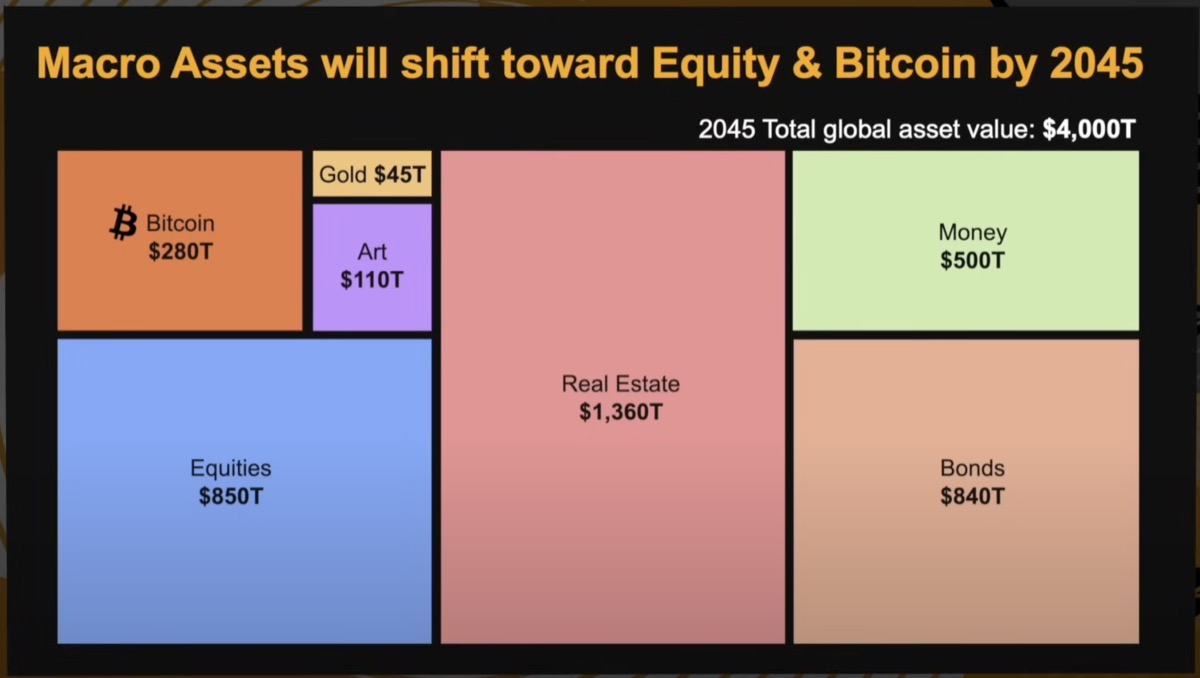
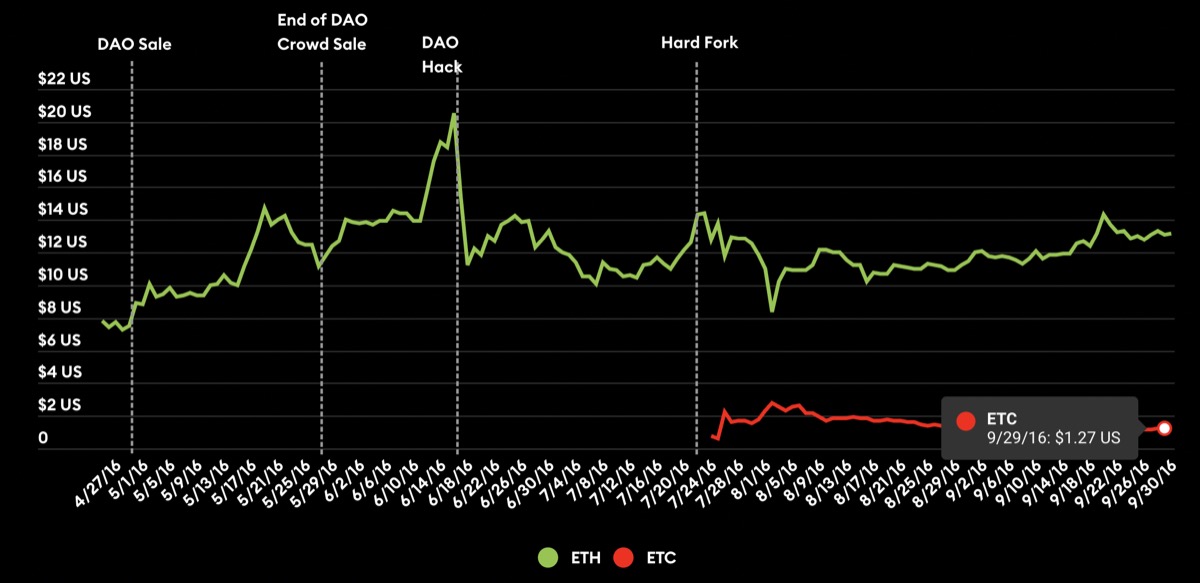
Ethereum biggest hack was in 2016, where 3.6 million ETH was stolen (now worth $11 billion)! But the blockchain took a hard fork, creating Ethereum Classic (ETC) where the hacker continue to hold the stolen tokens in the original Ethereum blockchain, which is still worth $90 million.
It was a hard lesson, because the hard fork is a precedence for more forks in the future. It is not as decentralized as it seems.
In the course of writing her book, Laura Shin found compelling evidence on who the DAO hacker could be!
He is the CEO of TenX, a crypto company in Singapore!
Highlights from Forbes
You can read the paid article on Forbes. I provide the highlights here:
appears to point to Toby Hoenisch, a 36-year-old programmer who grew up in Austria and was living in Singapore at the time of the hack. Until now, he has been best known for his role as a cofounder and CEO of TenX, which raised $80 million in a 2017 initial coin offering to build a crypto debit card—an effort that failed. The market cap of those tokens, which spiked at $535 million, now sits at just $11 million.
Hoenisch wrote in an email, “Your statement and conclusion is factually inaccurate.” In that email, Hoenisch offered to provide details refuting our findings—but never answered my repeated follow-up messages to him asking for those details.
A timeline of the events and hard fork.
This is how the hack worked.
Soon, the Ethereum community pinpointed the vulnerability that enabled this theft: the DAO smart contract had been written so that any time someone withdrew money, the smart contract would send the money first, before updating that person’s balance. The attacker had used a malicious smart contract that withdrew money (258 ETH at a time), then interfered with the updating of the contract, allowing them to withdraw the same ether again and again. It was as if the attacker had $101 in their bank account, withdrew $100 at a bank, then kept the bank teller from updating the balance to $1, and again requested and received another $100.
Laura had sources, and using blockchain analytics company Chainalysis, she found the trail.
In a final, crucial step, an employee at one of the exchanges confirmed to one of my sources that the funds were swapped for privacy coin Grin and withdrawn to a Grin node called grin.toby.ai.
The IP address for that node also hosted Bitcoin Lightning nodes: ln.toby.ai, lnd.ln.toby.ai, etc., and was consistent for over a year; it was not a VPN. It was hosted on Amazon Singapore. Lightning explorer 1ML showed a node at that IP called TenX.
Further research on Toby Hoenisch:
In May 2016, as it was finishing up its historic fundraise, Hoenisch was intensely interested in The DAO. On May 12, he emailed Hosp a tip (“Profitable crypto trade coming up”) to short ETH once the DAO crowdfunding period ended. On May 17th and 18th, in the DAO Slack channel, he engaged in a long conversation in which he made, depending on how you count, 52 comments, minimum, about vulnerabilities in The DAO, getting into various aspects of the code and nitpicking over exactly what was possible given the way the code was structured.
“He (the DAO hacker) really screwed the pooch. Reputation is way more valuable than money.”
For example, when asked if Hoenisch was into Grin (the privacy coins to which the hacker had cashed out) Hosp said, “Yes! Yes, he was. He was fascinated by that…I lost money because of those stupid coins! I invested in them because of him, because he was so fascinated by them.”
Later, Hosp pulled up chats from August 2016, in which Hoenisch seemed excited about the price of ETC, the coin held by the hacker after the ethereum fork.
Recalled a still astounded Hosp: “For some weird reason, he was quite well aware of what was happening…He understood more of the DAO hack when I asked him what had happened…than I had found on the internet or anywhere.”
The Forbes video